
Because Twitter is introducing its paid subscription package Twitter Blue, the company has been implementing a number of new tools alongside a number of restrictions. For example, the SMS two-factor authentication will be restricted to only those users who have purchased the monthly service.
Two-factor authentication is a subset of multi-factor authentication (also known as MFA), which adds an additional layer of protection to your social media profiles in addition to the username and password you already use.
Prior to March 20, this safety function could be used on Twitter at no additional cost; however, after that date, only Twitter Blue subscribers will have access to it.
People who do not have a Twitter Blue subscription have been informed about the new update and given a deadline of March 19 to remove the two-factor authentication in order to prevent losing access to the microblogging platform entirely.
When you log in with two-factor authentication (2FA), in addition to entering your password, you are also required to input a code or use a security key. This additional process helps to ensure that no one but you is able to access your account other than yourself.
After March 20, 2023, we will no longer allow users of Twitter who are not subscribed to Twitter Blue to use text messages as a manner of two-factor authentication. At that point, two-factor authentication via text message will be disabled for accounts that still have it enabled. According to a statement released by Twitter, turning off text message two-factor authentication will not automatically disconnect your phone number from your Twitter account.
If non-Blue users do not implement a different authentication technique, Twitter has stated that it will disable 2FA entirely. Users have the option of bolstering the safety of their accounts by utilizing either a security key or an authentication program. This will allow them to circumvent the issue.
How to Change Settings for Two-Factor Authentication If you do not wish to purchase Twitter Blue but are scared of losing your account or don’t know how to log in without using two-factor authentication, then there is no need for you to worry. Getting rid of two-factor authentication is not too difficult.
To begin, you will need to launch Twitter either on your mobile device or through a computer. Select Account Access & Security from the drop-down menu.
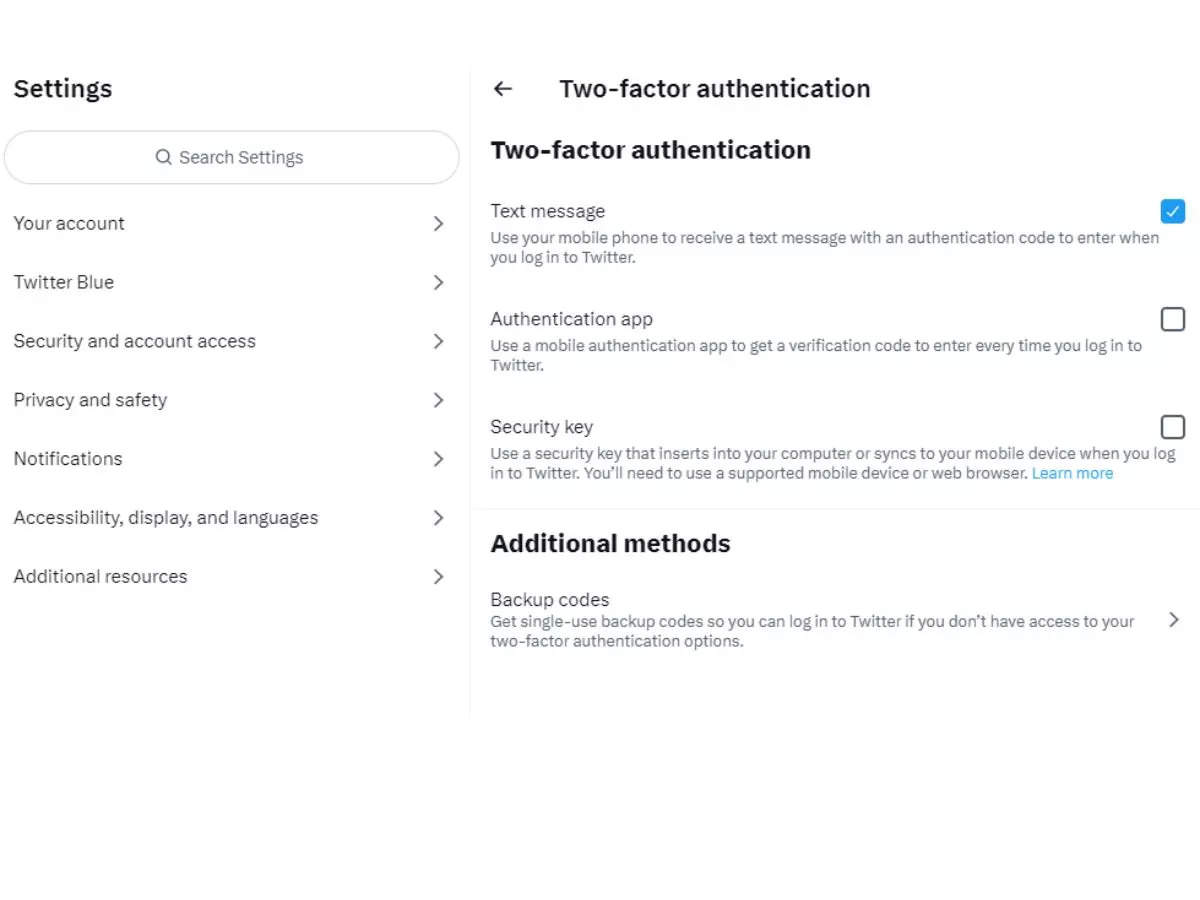
Now navigate to the Security menu and select Two-factor authentication from the drop-down menu.
You will now have three choices available to select from.
• Receive a text message on your mobile phone containing an authentication code that you will need to input when you log in to Twitter. This method requires the use of your mobile phone.
• Authentication app — This feature requires the use of a mobile authentication app in order to obtain a verification number that must be entered each time you log in to Twitter.
• Security key — When you register in to Twitter using this method, you will be asked to insert a security key into your computer or sync it to your mobile device.
Select the authenticator app of your choosing, such as Google Authenticator or Microsoft Authenticator, in order to log in to the authentication app. After that, log into your Twitter account and begin following the same groups of people as before. After you have decided which application to use, you will need to enter your password and then select the Confirm button.
If you haven’t confirmed your email address with Twitter yet, the microblogging platform will give you an email containing a confirmation code and a link that will take you back to the social network platform. If this is the case, you can expect to receive the email shortly.
You need to have a tangible authentication key, such as YubiKey, in order to have a security key. However, you need to make sure that the key supports your browser, which could be Chrome, Safari, Firefox, or something else. Now navigate to Twitter and follow the instructions that were previously discussed, making sure to click on the Security Key button.
Now Twitter will inquire about your password, and if you haven’t already validated your email address with the platform, you’ll receive an email containing a code and a link that will take you back to the site. After you have finished reading the instructions and proceeded on to the next step, you will need to either connect the key to the USB port of your computer or sync it using Bluetooth or NFC.
Two-factor authentication > Manage security keys is where you’ll find your security key once it’s been configured properly and added to the system.